What is Access Control Systems?
The term “Access Control System” actually refers to systems officially referred to as “point monitoring and access control systems” because they not only control electronic locks on doors, control access on elevators and elsewhere, but also monitor alarms. While there are some small panel-based alarm systems that also control card readers on doors, this article refers generally to the larger PC based point monitoring and access control systems.
Most of these are powerful systems. Even the smallest of the major systems used in larger museums is generally capable of meeting the needs of very large institutions simply by unlocking features in the software or upgrading the server to one a bit more robust. Some museums have made the mistake of buying less expensive access control systems because they appear to do the same things as the more expensive leading brands and because they are powerful enough for the museums current and future needs. The mistake some make is to buy one of the systems that is not UL listed for alarm monitoring or to buy a system that will not be around in a year leaving them with an orphaned product to find service for.
Underwriters’ Laboratories (UL) is a testing organization owned by the insurance industry. They test everything from alarm systems, and their individual components, to toasters and verify that they perform to their standards for safety and reliably, A toaster, for example, toasts bread and doesn’t catch fire doing so. All alarm and access control systems used in museums must be “listed” for their purpose. “Listing” means they have been approved for the use advertised and meet the standards UL has established for them. The insurance industry established UL so they know that specific products intended to reduce risks do so. And the insurance industry requires that all alarm and access control systems be UL listed.
An access control system can be listed for access control but not for alarm monitoring. Nearly all are listed for access control but many smaller or less expensive systems are not listed for alarm monitoring. Surprisingly, consultants have reported to us that a few of their clients have, for whatever reason, chosen to buy non-listed systems. This could affect many things from their insurance coverage to their ability to borrow works of art. This is not unlike buying a home made burglar alarm panel that may or may not have been built to minimum UL standards. No one would do it but some seem to think that when a system is part of an access control package that this doesn’t matter. It does. One brand used for years by many major museums could not electronically supervise the alarm circuits meaning anyone could cut the wire when the alarm detector was off such as during the day when the museum is open, and the detector would no longer work when turned back on.
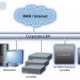
Here is how they work. The heart of these system is a unit we will call a controller. Each product brand is different but controllers generally can handle a specific number of alarm points (generally, 32 or more) and a specific number of access controlled doors (generally, four or more). Larger products may actually handle 128 alarm inputs, 32 alarm outputs and sixteen doors on one controller. Even though it is in a metal box mounted on a closet wall, each controller is a computer and each works independent of any others that are networked to it. When your needs exceed the capacity of the controller you can simply buy a new controller, and network it to the others. This adds capacity to your hardware. Your service provider then sells you a software key that unlocks more software capacity on your system.
A PC-class server runs the master software but each controller uses its own operating system software. With large enterprise systems using hundreds of controllers, entire nationwide banking systems can be accommodated on a single server and each building can be independent of the server if it has to be. PC operator terminals are the means by which we humans interface with this extremely powerful computer network. Basically, all that the PC does is translates what the network controllers are doing for us humans to understand. When the server and the operator terminals fail for any reason, the system is capable of continuing operation through its network of controllers. It just isn’t possible for us humans to interface with it unless we think very very fast in binary!
Let’s look at the two major functions of the system: alarm monitoring and access controls. The alarm portion of the access control system works just like any other alarm system. Any type of detector or contact connects to the controller by a wire and there are wireless options, too. When an alarm occurs on a detector it sends a signal to the controller and the controller’s output causes a separate dialer to call the central station just like a small alarm system does.
The access control portion of the system uses reader controller boards, lock power supplies, and other add on components to control card readers, keypads or even biometic readers like palm print, fingerprint or retina readers. They can interface with the elevator control package of your elevators and then control elevators button by button and floor by floor.
The server contains a database of users. Each user is programmed with access to specific readers during specific hours of the day or days of the week. Your card may open collection storage but mine might not.
Various types of access cards or fobs can be used. The most common type uses Weigand technology and is called a Weigand proximity card. A reader emits a specific inaudible frequency that the cards are sensitive to. When the card is presented to the reader, the reader, responds with a corresponding handshake signal. When the two make contact the reader asks the controller if the card is authorized to open the door at this moment. The controller checks its database. If it is, the door lock releases. If it is not, the controller notifies the server that a breach is occurring, and that alarm appears on the monitor with instructions for the guard to take action. This can display in any language as well as on graphic floor plans.
Access control systems do other things, as well. Some interface with the ID card printer so that you don’t need to maintain a second database of active employees. And others interface with the CCTV system.
When an access control system is integrated with a CCTV system it is possible for a camera viewing a door to call up a camera image to a monitor when a card is presented to the reader. Or, a camera can call up when motion is detected in a space protected by a motion detector. You can program the system to do virtually anything like trip a pager or send a text message to a phone.
Some systems integrate other products like lobby management systems and electronic key boxes.
The primary difference between an alarm control panel that is not PC-based and an access control system’s alarm component, is that with a panel based system, alarms can only be controlled-turned on and off-in groups and not individually. (A few systems do allow you to turn individual alarms on and off but this is cumbersome). But with access control systems, any individual alarm point can be turned on and off individually. They can even be programmed to turn themselves on and off.