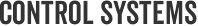
Access control Management System
You also agree that your personal information may be transferred and processed in the United States, and that you have read and agree to the Terms of Use and the Privacy Policy.
Access control doesn't just happen. As you saw in the first installment of this Hot Spot Tutorial, securing corporate resources demands careful selection and integration of server, software and identification technologies. But an access control project doesn't stop with things like multifactor identification - it requires proper configuration to establish roles and policies for the identities of each user. That configuration then has to be managed over time to accommodate individual users and the evolution of your client's business. In this second chapter, you will learn various aspects of access control management and get a closer look at some of the business opportunities available to security solution providers.
There are three access control realms that must be managed: identities, rights and reports. These correspond to the areas of authentication, authorization and audit described in part one of this tutorial. Identities that need to be managed include user names, passwords, security tokens and other factors that authenticate a user. For example, assigning or resetting a user's password is one simple access control management task.
Managing identities has become dramatically more complicated as organizations take on more applications and support additional computing or storage resources. This has led to the introduction of identity management (IDM) technologies that organize the proliferation of user accounts under a single manageable identity. "Companies are moving to that model where you're managing identities and then underneath that you have logins and passwords, " said Andrew Plato, president of Anitian Enterprise Security, a security solution provider headquartered in Beaverton, Ore.
The second realm of access control, the management of user rights, ensures that a user can only access the minimum corporate resources that are appropriate for their job. While user rights can be assigned for each user, it's more common to manage rights through rules and policies established for the client's organization. For example, you may create a human resources (HR) group and a finance group for your client, each with different rights, and then add HR employees to the HR group and accounting employees to the finance group. Controlling the rights of each group and the users in each group is an important part of access control management.
While rights management isn't yet as sophisticated as identity management, solution providers still may be challenged by interoperability problems within the client's environment - particularly with older client organizations that have been through numerous technology and growth/acquisition cycles. "You can have applications and databases and systems that cut across many different manufacturers, and they may not talk well together, " Plato said, noting that automating rights management can be difficult in that situation, leaving solution providers and their clients with time-consuming, error-prone manual processes.
Rights management can also be delegated to the cloud. Access rights routinely extend outside of the client's organization to remote applications and storage. Solution providers will need to ensure that user rights are just as well-defined outside of the organization as they are within the organization.
Auditing, the third aspect of access control management, involves reviewing and analyzing reports that track user behavior, along with any changes made to rules, policies and other aspects of the client's environment. As internal security incidents become more frequent, some solution providers are implementing tools that can track administrative behaviors.
"There's a hot product technology in database auditing that audits the database admins, " said Robi Papp, strategic accounts manager with Accuvant Inc., a security consulting organization headquartered in Denver. "You want to audit the security personnel as well." Papp said that implementing a quorum system to authorize changes to user access control can prevent collusion within your security framework. "If [admins] have the keys to the kingdom, you could have a great user access control system - but if the manager of it is the thief, you're still in trouble, " he said.
Solution providers should also help clients identify and implement a range of supplemental tools to automate and manage access control tasks. Automated password reset tools are a popular option that is often rolled into more comprehensive tool sets. "The more that you can give a client the ability to manage themselves, the happier they are going to be, " said Dave Sobel, CEO of Evolve Technologies, a solution provider headquartered in Fairfax, Va. "You don't want them waiting on an engineer for simple things like password resets."
Access control opportunities and cautions for solution providers
There is ongoing revenue potential in access control management services. "Solution providers are up against organizations that have the in-house skill sets to deploy and manage access control systems, " said Allen Zuk, president and CEO of Sierra Management Consulting LLC, an independent technology consulting firm. "There are considerable opportunities for solution providers to support the SMB players who may not have sufficient skill sets in-house and may be looking to outsource the service." However, a solution provider must avoid deployment and configuration mistakes to be successful with access control projects or ongoing management tasks.
First, solution providers need to understand the client's unique business needs and strategy, as well as embrace the client's compliance obligations. This will help providers develop the best policies without inconveniencing users or otherwise impinging on the client's business. Access control affects many aspects of an IT infrastructure, so errors in deployment or configuration will have an immediate and noticeable impact on the end users - you cannot hide an access control mistake. Clients are beginning to realize that there is a price tag attached to incorrect policies.