Management control Systems definition
An identity access management (IAM) system is a framework for business processes that facilitates the management of electronic identities. The framework includes the technology needed to support identity management.
IAM technology can be used to initiate, capture, record and manage user identities and their related access permissions in an automated fashion. This ensures that access privileges are granted according to one interpretation of policy and all individuals and services are properly authenticated, authorized and audited.
Poorly controlled IAM processes may lead to regulatory non-compliance because if the organization is audited, management will not be able to prove that company data is not at risk for being misused.
Why you need IAM
It can be difficult to get funding for IAM projects because they don’t directly increase either profitability or functionality. However, a lack of effective identity and access management poses significant risks not only to compliance but also an organization’s overall security. These mismanagement issues increase the risk of greater damages from both external and inside threats.
Keeping the required flow of business data going while simultaneously managing its access has always required administrative attention. The business IT environment is ever evolving and the difficulties have only become greater with recent disruptive trends like bring-your-own-device (BYOD), cloud computing, mobile apps and an increasingly mobile workforce. There are more devices and services to be managed than ever before, with diverse requirements for associated access privileges.
With so much more to keep track of as employees migrate through different roles in an organization, it becomes more difficult to manage identity and access. A common problem is that privileges are granted as needed when employee duties change but the access level escalation is not revoked when it is no longer required.
This situation and request like having access like another employee rather than specific access needs leads to an accumulation of privileges known as privilege creep. Privilege creep creates security risk in two different ways. An employee with privileges beyond what is warranted may access applications and data in an unauthorized and potentially unsafe manner. Furthermore, if an intruder gains access to the account of a user with excessive privileges, he may automatically be able to do more harm. Data loss or theft can result from either scenario.
Typically, this accumulation of privilege is of little real use to the employee or the organization. At best, it might be a convenience in situations when the employee is asked to do unexpected tasks. On the other hand, it might make things much easier for an attacker who manages to compromise an over-privileged employee identity. Poor identity access management also often leads to individuals retaining privileges after they are no longer employees.
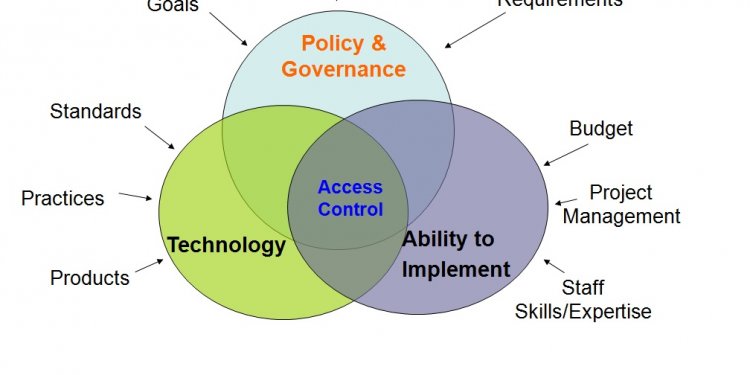
What should an IAM system include?
IAM solutions should automate the initiation, capturing, recording and management of user identities and their related access permissions. The products should include a centralized directory service that scales as a company grows. This central directory prevents credentials from ending up recorded haphazardly in files and sticky notes as employees try to deal with the burden of multiple passwords for different systems.
IAM systems should facilitate the process of user provisioning and account setup. The product should decrease the time required with a controlled workflow that reduces errors and the potential for abuse, while enabling automated account fulfillment. An identity and access management system should also provide administrators with the ability to instantly view and change access rights.
An access right / privilege system within the central directory should automatically match employee job title, location and business unit ID to manage access requests automatically. These bits of information help classify access requests relevant to employees’ existing positions. Depending on the employee, some rights might be inherent in their position and automatically provisioned, while others may be allowed upon request. In some cases, reviews may be required. Other requests may be denied except in the case of exemption or may be outright prohibited. All variations should be handled automatically and appropriately by the IAM system.
An IAMS should set workflows for managing access requests, with the option of multiple stages of reviews with approval requirements for each request. This mechanism can facilitate setting different risk level-appropriate review processes for higher-level access as well as reviews of existing rights to prevent privilege creep.
IAM products
One Identity Manager from Dell combines easy installation, configuration and use. The system is compatible with Microsoft SQL and Oracle database systems. According to Dell, the self-service product is so user-friendly that employees can manage all stages in the IAM life cycle without requiring help from the IT department. The product suite also includes Cloud Access Manager, which enables single sign-on capabilities for a variety of Web application access scenarios.
F5 Networks' BIG-IP Access Policy Manager has highly-reviewed service and support. The software is part of the BIG-IP multilayer switch system, which is available in appliance and virtualized systems. The Policy Manager allows access through all major web browsers, saving workstation configuration time.
Tools4ever's Self-Service Reset Password Management is ranked highly for ease of installation, configuration, management and service. The tool allows admins to create their own “forgot password” link for users and specify numbers of security questions. This self -service password tool has been demonstrated to reduce the need for password reset calls by as much as 90 percent.
IBM's Security Identity Manager is designed to be quick and simple to deploy and to be compatible with other products. The software supports Microsoft Windows Server, SUSE Linux Enterprise Server, Red Hat Enterprise Linux and IBM's own AIX, as well as most common operating systems, email systems, ERP systems and cloud applications such as Salesforce.com. The included toolkit simplifies the integration of custom applications. Creation and modification of user privileges are automated through a rules-based system and access rights can be automatically added or removed for individual users based on changes in business roles. Permissions can also be applied for groups.