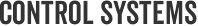Cybersecurity for Industrial Control Systems
Today’s industrial control systems (ICS) face an array of digital threats. Two in particular stand out. On the one hand, digital attackers are increasingly targeting and succeeding in gaining unauthorized access to industrial organizations. Some actors use malware, while others resort to spear-phishing (or whaling) and other social engineering techniques. Those tactics notwithstanding, most of the major ICS security incidents we heard about in 2016 fortunately caused only disruption, not destruction, to the organizations they affected.
On the other hand, Trend Micro’s researchers found, for example, that actors can leverage passive intelligence to eavesdrop on unencrypted pages sent between beepers used in industrial environments. Those attackers can then use that stolen information to conduct social engineering attacks, break into an organization, or create false alarm scenarios that could affect industrial operations.
To protect against those threats, it’s important that companies take adequate steps to create effective industrial security programs and prioritize organizational risks. Belden has developed a 1-2-3 approach to industrial cyber security, organized to help reduce complexity, prioritize risks and get started securing the industrial network, endpoints and control systems.
1. Securing the Network
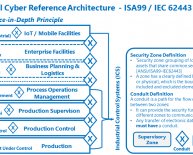
Industrial organizations that want to secure their networks should begin by making sure they have a good network design with well-secured boundaries. Once they complete that initial step, enterprises should segment their networks by implementing the ISA IEC 62443 standard, secure all of their wireless applications, and deploy secure remote access solutions to help with fast troubleshooting and problem-solving.
“Monitoring the security status of a network is common practice for IT security teams but less common in operations environments…[there is also] value in monitoring industrial network infrastructure equipment such as routers, switches, gateways etc. These systems connect the segments and can be compromised. They need to be assessed, a baseline taken and a monitoring effort applied.”
2. Securing the Endpoints
OT professionals might feel their organization’s endpoints are protected against digital attacks by perimeter firewalls, proprietary software, specialized protocols, and airgaps but that just isn’t the case. The moment employees, contractors or supply chain personnel walk in with their laptop or a USB to conduct maintenance, these safeguards are bypassed.
“To mitigate OT attacks, PC-based endpoints in the OT environment need to be protected, and organizations need to defend their IT endpoints against attacks that traverse over to the OT environment. An overarching endpoint security strategy needs to be in place for OT and IT environments.”
A starting place for many organizations is to gather and maintain an accurate inventory of all endpoints’ hardware and software, tracking the vulnerabilities in OT assets, assuring secure and hardened configurations are in place at each endpoint, and monitoring and alerting on unauthorized changes.
3. Securing the Controllers
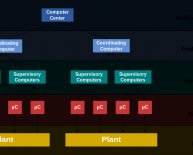
In every industrial environment, there are physical systems – mechanical devices such as accuators, calibration devices, valves, and an array of sensors for temperature, pressure, etc. that interact with the physical world. Bad actors have gained access to these mechanical devices in many documented cases, causing those systems to malfunction, but they have no direct way of doing so without gaining access to the control level.
“…[P]hysical systems are connected back to a type of specialized computer that actually controls it. It is these specialized computers that make the bridge between controlling the physical systems and receiving programming or instructions from a network. These are the industrial controllers, and they are the systems being targeted to create physical damage or disrupt a revenue generating industrial process in cyber attacks. Industrial controllers come in different varieties, but you will hear terms such as PLC (programmable logic controllers) and DCS (distributed control systems) used commonly to refer to different types of these.”