Physical Access Control Systems
How many managers think that it makes no sense to spend money protecting information that can be reconstructed? What can really happen? Theoretically, anything and everything from the abuse of workers (through natural disasters and industrial espionage) to terrorist attacks. Is our company is prepared for this? Imagine this scenario: at your company, no one is around in the middle of the night to hear the sound of breaking glass and quick steps. In the morning, the first employee appears at work and calls the police after spotting the mess. According to police, it was a random act of vandalism. Two weeks later the president convenes a meeting; it turns out that the local newspaper is running a story about your product, and has just revealed that the project has gone millions of dollars over budget. It turned out that a random act of vandalism was really an act of industrial espionage. The intruder had attacked a bootable distribution of Linux operating system and copied the files that belong to the victim company.
Of course, this situation could have been prevented if there were appropriate procedures in place. In practice, anyone who has physical access to a computer can take over your system in seconds. Therefore we will discuss some physical security procedures to try and minimize the risk of attack by introducing appropriate access controls. Please note that each access control has three aspects: physical, administrative, and technological development.
Physical Security Schema
Work on physical security mainly focuses on the physical protection of information, buildings, personnel, installations, and other material resources. Additionally, physical security covers issues related to processes prior criminal activities, espionage, and terrorism. What factors can develop into the biggest direct threats?
- Staff – dismissal, strikes, illness.
- Sabotage and vandalism.
- Hardware failures.
- Natural disasters – tornadoes, earthquakes, floods, and tsunamis.
- Man-made disaster – terrorism, arson, bombings.
- Loss of access to electricity, air, and water.
Once we know what threatens us personally, we can begin to consider the best methods of protection. For example, in the case of a power outage, you should have a backup generator to maintain the critical elements of the system, and lighting for employees as well as a backup phone system. If there is a hardware failure, having certain spare parts on hand can be incredibly useful, as can having a well-designed service contract. In addition, it is a good idea to familiarize yourself with the industrial-safety laws of the country in which you’re operating.
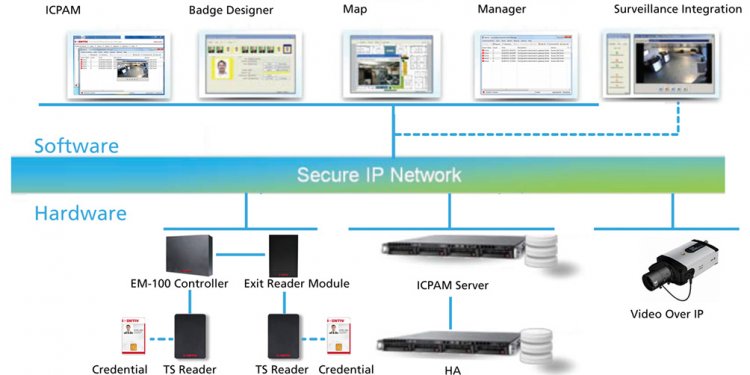
Physical access controls are mechanisms that are designed to minimize the risk of injury. A simple example is a good fit on the door lock, which will discourage many potential thieves. The installation of biometric sensors, such as iris scanning or fingerprint recognition, can make even the most determined intruder falter while trying to gain access to a guarded place. Sometimes all that is needed to resolve the issue is a mechanism to provide enough time to contact the appropriate authorities. But the door is not the only object that should be closed.
We should consider closing off access to laptops, desktops, and servers. Like many employees, I just do not know when an intruder enters the building, and then runs away unrecognized with a laptop under his arm. Such situations happen very often. More and more companies are taking the precaution of removing all drives from individual computers to prevent the use of USB, COM, LPT theft, and instituting additional BIOS password protection just to prevent employees from installing personal software, gaining unauthorized access, and ultimately, participating in theft. One possible scenario to tighten security is to use the terminal server and a bootable Linux distribution. Also excluded are DHCP, preventing problems with spyware, malware, or viruses usual.