Access Control System
PAGE 3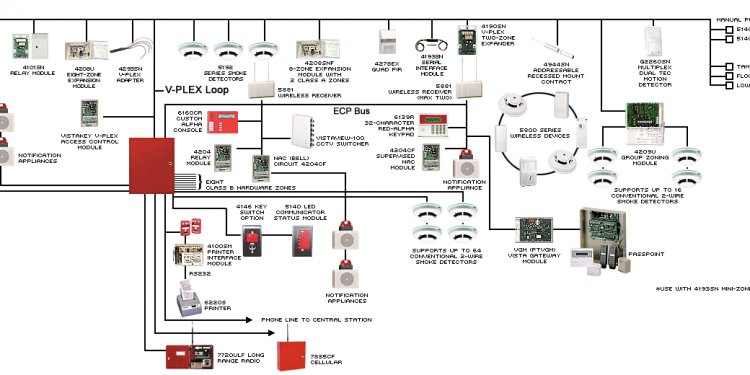
Honeywell Access Control System PDF
Honeywell’s OmniProx™ family is a complete line of 125 kHz HID compatible proximity readers that delivers outstanding and consistent performance in a small package with attractive styling and colors to fit any décor. All OmniProx™ readers (except the OP90) include three bezels: black, charcoal gray and ivory and are constructed with rugged polycarbonate materials potted for…
Read more
Access Control System Architecture
ADepartment of Computer Languages and Systems, University of Granada, SpainbDepartment of Computer Languages and Systems, University of Cádiz, Spain Abstract One of the most important characteristics of current enterprise systems is the existence of collaborative processes where different users/subsystems communicate and cooperate in order to carry out common activities. In…
Read more

Swipe Card Access Control Systems
Traditional swipe card access control systems have for may years used the magnetic swipe card and it will continue to be popular for may years to come as systems in the market with may existing cards are upgraded and refurbished. The magnetic card is also still a very cost effective card technology. Lock-tec are happy to supply and install magnetic swipe card systems while…
Read more

Access Control System Diagram
IP Door Access Control Systems are easy to install and provide excellent flexibility, yet many people who are used to the older type systems have concerns about using them. This article tries to take the mystery out of network attached door access control systems, and describes how very easy they are to install and use. You will find that all the signals that were on multiple…
Read more

Barcode Access Control System
Protecting company assets and employees is a concern every business has regardless of their size. Security is a greater concern than ever and advances in access control technology have moved well beyond the traditional lock and key method. Electronic access control provides improved security and better management of your facility access by utilizing secure IDs that can be tracked…
Read more

IP Based Access Control System
HID Global s Networked Access Solutions provide a flexible, open architecture, IP-enabled platform for deploying a broad range of access control systems. Whether you need to control two doors or manage hundreds of doors at multiple facilities, HID Global s versatile and easy-to-use networked access control solutions bring intelligence to the door while protecting the value…
Read more
Access Control in Operating Systems
Access control mechanisms (ACMs) have been widely used by operating systems (OSes) to protect information security. However, it is often challenging to evaluate and compare the quality of protection (QoP) of ACMs, especially when they are deployed on different OS platforms. This article presents an approach to quantitatively measure and compare the quality of ACMs, which provides…
Read more
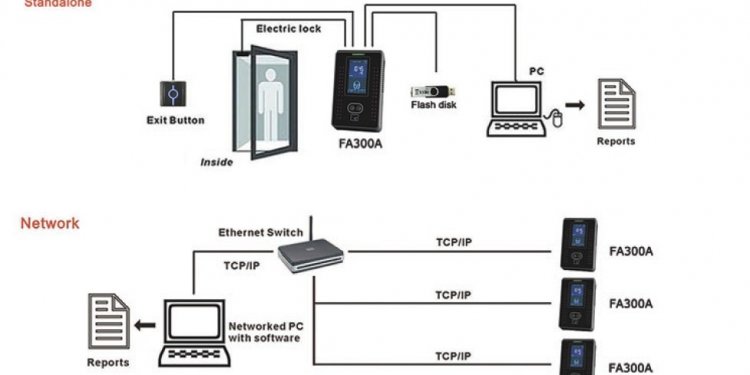
Smart Card Access Control System
HID Global’s pivCLASS® Government Solutions portfolio is an extensive product family that makes it easy for U.S. Federal Government, government contractors and other facilities to comply with security regulations and to use their Personal Identity Verification (PIV) card and other smart cards for physical access control, resulting in compliance, interoperability and high security…
Read more

Access Control Systems Manufacturers
The 3 main drivers for growth are the continuing move to IP technology, the integration of Access control with Identity Management and Wireless Controls. Access control through a standard card reader system is a weakness, particularly at a time when risk of corporate theft, malicious damage and terrorism has increased. The need for a more secure system incorporating biometric…
Read more
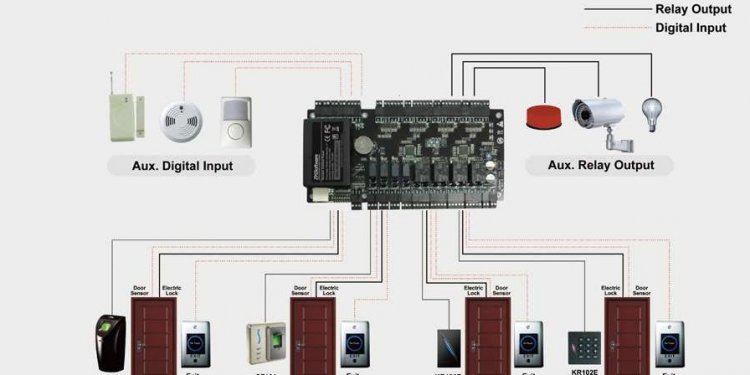
RFID Proximity door Entry Access Control System
Shop the extensive inventory of home automation equipment including door entry system access controls! As the world becomes less secure, businesses and consumers are becoming more aware of their own security measures and the options available for controlling their premises. Access control systems have evolved greatly over the past 10 to 15 years in a direct response to this…
Read more
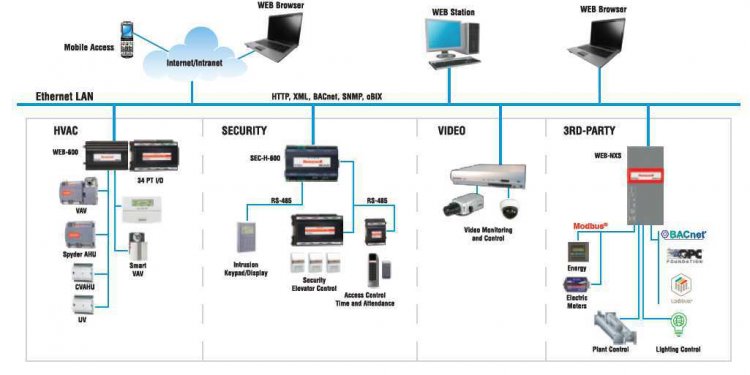
Building Access Control Systems
Editor s note: ADT recently announced the completion of a merger with Protection 1. When ADT and Protection 1 complete this brand integration, we will update our access control systems reviews to reflect that information. The top performers in our review are Protection 1, the Gold Award winner; Tyco, the Silver Award winner; and Brivo, the Bronze Award winner. Here’s more on…
Read more

Controlled Access Systems
(a) Controlled access zones. (1) When used to control access to areas where leading edge and other operations are taking place, the controlled access zone shall be defined by a control line or by any other means that restricts access. Signs shall be posted to warn unauthorized employees to stay out of the controlled access zone. (2) When control lines are used, they shall be…
Read more
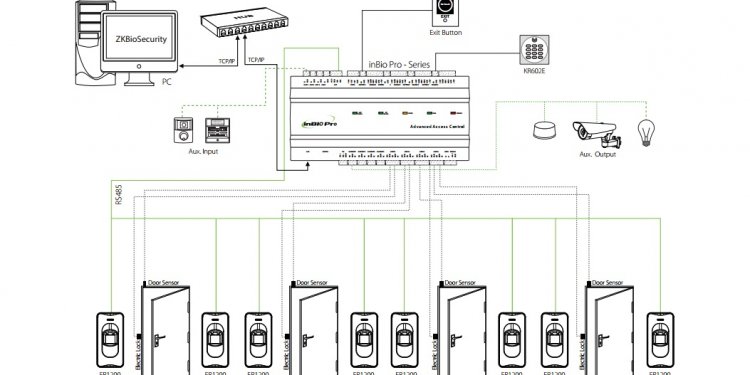
Terminal Access Controller Access Controller System
TACACS (Terminal Access Controller Access Control System) is an older authentication protocol common to UNIX networks that allows a remote access server to forward a user s logon password to an authentication server to determine whether access can be allowed to a given system. TACACS is an encryption protocol and therefore less secure than the later TACACS+ and Remote Authentication…
Read more

CCTV and Access Control Systems
Security USA™ has consistently investigated the latest innovations so we can offer our clients the most cutting edge technology. Closed Circuit Television (CCTV) An invaluable asset in the world of security is the ability to use CCTV (Closed Circuit TV) to conduct surveillance. Using a CCTV system, individuals, companies and organizations can instantly reduce or even cease…
Read more

What is an Access Control Systems?
Now more than ever, tight security is paramount in just about any business establishment in Mesa — regulations are increasingly stringent regarding data privacy and security. You must be extremely vigilant as to who has access to your building and other “off-limits” areas within your facility. Easy, unmanaged access to your building can also place you at higher risk of burglary…
Read more